Wireshark can be used for a deeper
Wireshark can be used for a deeper understanding of what has happened on the network, but it can also be utilized for reconstructing certain artifacts.
- In this project, you have been given access to a PCAP file from FICBANK to analyze. As you are analyzing this data in Wireshark, note some of the interesting interactions you find within the traffic.
- You can examine some HTTP traffic in the PCAP file you were given for analysis by entering “http” into the Wireshark search bar.

- When you see an image in PCAP traffic, it can be reconstructed with the following steps:
- Right click on one of the packets with the HTTP protocol and select “Follow –> HTTP Stream”.
- Take note of what you see here in the traffic, as it is important to understand what is happening in this interaction.
- Right click on one of the packets with the HTTP protocol and select “Follow –> HTTP Stream”.

- Click “File” on the Wireshark menu and select “Export Objects –> HTTP”.
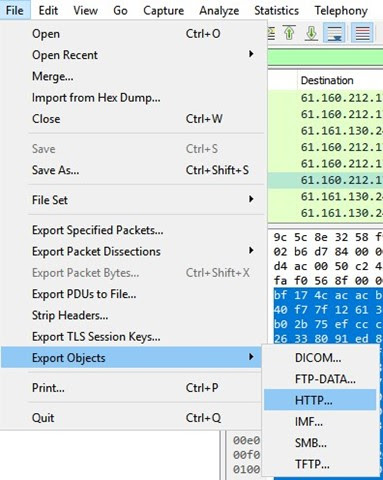
- You should see several images within the popup. Select “preview” on each image to have Wireshark reconstruct and download them. This should open a directory where the images are saved.

-
What is this traffic sample telling you? What information can you piece together from it? Think critically about the pertinent information, and note anything useful for your report.
Exercise 2 TrID ( I am unable to install it. When i click on the link to install all i see are zip files).
TrID is a fantastic open-source tool for enumerating filetypes. Attackers may change a malicious file’s extension in order to perform actions such as uploading to a web server, avoiding endpoint detection tools, and tricking monitoring applications into thinking it is a legitimate file. Once the file is hosted on the network, it can be changed back to its original filetype and executed for exploitation or post exploitation.
- Download and install TrID from its source page. This should create a folder called “trid_w32”. Within this folder you should see the trid.exe and triddefs.trd.
- If you don’t see the triddefs.trd file, please go to the TrID webpage and download the latest version. Place it in this folder.
- Thinking back to the Wireshark images we generated, something seems off about them based on their HTTP stream. Let’s make sure they aren’t malicious files.
- Create a new folder in a different directory, as Wireshark saves images in a temporary directory that will be erased on reboot. Move images to this new directory, along with the files from the trid_w32 folder.
- Open the command prompt and run TrID against the images you reconstructed from Wireshark. Take note of some of the different flags you can add to the TrID command line executable.

-
Record what these file types are and save them as part of your evidence gathering process.
Logs are going to be essential to understanding how a compromise happened, what reach the attacker had into the network, and what may have been accessed or egressed from the network. Detailed logs can also help an analyst pinpoint where the attacks came from with a certain level of confidence, but always remember that attribution can become exceedingly difficult if you are investigating a sophisticated attack. For the purposes of this course, we are going to focus on the potential compromise itself, whereas a digital forensics course can detail more of the attribution aspect of pinpointing an attacker’s origin.
- Note the log files you were given access to from the previous lab. What deductions have you made from these logs thus far?
- Now we need to do a deeper analysis using different techniques to continue piecing the story together for our AAR.
- Some popular methods for parsing and searching logs in a native Linux environment are:
- sed
- awk
- grep
- For large scale log analysis, any analyst will quickly learn that these types of native tools are great for searching and manipulating data but fall short on large datasets. It is important to have a fundamental knowledge of them for sorting smaller datasets, but you should take a look at some of the open-source log management tools on the market today.
- Graylog
- Logcheck
- ELK Stack
- Revisit the “access-2” logfile. What can you correlate between the logfile and your Wireshark output? Are there any similarities?
- Try to piece the story together based on the information you see from the provided artifacts.
- Where does it look like the attack originated from?
- What did the attacker attempt to do?
- Compile your findings and incorporate them into your deliverables for this project.
Lab Resources (Application Websites)
******CLICK ORDER NOW BELOW AND OUR WRITERS WILL WRITE AN ANSWER TO THIS ASSIGNMENT OR ANY OTHER ASSIGNMENT, DISCUSSION, ESSAY, HOMEWORK OR QUESTION YOU MAY HAVE. OUR PAPERS ARE PLAGIARISM FREE.*******."

